An important product of bitcoin mining as we have seen is the creation of new bitcoin, but equally or even more important than that is the blockchain as a result of the mining process.
Overview of the Blockchain
First, we take a look at the general features of what makes the blockchain special.
As each cryptocurrency has its own blockchain (e.g. Ethereum blockchain, Litecoin blockchain etc.), unless otherwise mentioned, the term blockchain in the following text is taken to mean the Bitcoin blockchain.
- The blockchain is a decentralised public ledger which keeps a record of every single bitcoin transaction across a peer-to-peer network since the inception of Bitcoin in 2009.
- A block of transactions compiled by the miner roughly every 10 minutes is added to previous blocks of transactions dating all the way back to 2009 in a series or a chain of blocks, hence the term blockchain. See Mechanism of the Blockchain below.
- It is immutable and thus cannot be altered. As such, it is an append-only database, i.e. information can only be added to the records, and cannot be subtracted or modified along the way. See Security on the Blockchain below.
- The blockchain public ledger is accessible 24/7 by anyone and is a means to verify if a bitcoin payment between two bitcoin addresses has been made and exactly when it was made. See Section 2.6 Checking Transactions under Chapter 2.0.
- The application of blockchain goes far beyond than just for currency and payment use. It could also be used in areas of smart contracts, intellectual property, voting and to maintain a trusted audit trail of ownership for a vast range of assets such as land, real estate, vehicles etc.
- Watch the following video for a quick overview of what the blockchain could potentially be used for and how it could change the way we do things in the future:
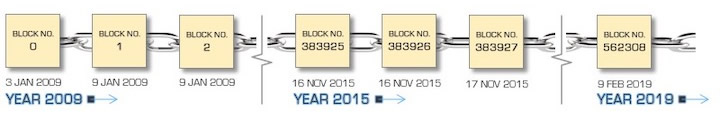
Fig. 1.6a New blocks are added to previous blocks every 10 minutes all the way back to the genesis block on 3rd January 2009 in a chain-like series, hence the term blockchain.
Mechanism of the Blockchain
Next, we look at how the blockchain is created as a result of the mining process.
- A user initiates a bitcoin transaction to another user. At the same time, hundreds or even thousands of users are performing such transactions.
- These transactions are collectively placed in a blockA virtual container of bitcoin transactions created about every 10 minutes on average..
- The block is broadcasted to all the nodes of the Bitcoin network, including the miners.
- The miners attempt to solve the block puzzleA cryptographic mathematical challenge that miners need to solve for each block to validate the contained bitcoin transactions and to earn the mining rewards. by applying nonces32-bit random numbers used in a cryptographic communication only once and churned out by miners to derive a block hash that is less than or equal to the current target of the network. to the block hash to achieve the desired result.
- The first miner to solve the block puzzle broadcasts the solution to the network. All other miners verify that the result is true and correct.
- Upon successful validation, the block is added to the blockchain, linking it to previous blocks that came before it.
- All the transactions in the block get verified and eventually confirmed.
- The successful miner receives the block reward and all transaction fees in the form of bitcoin.
- The next block of transactions is prepared for validation to be added to the blockchain and the process repeats.
- The above takes place approximately every 10 minutes on average.
Security on the Blockchain
The blockchain has often been touted as a highly secure public ledger resistant against hacks and attacks. To what extent is this true? We consider the following points:
- Bitcoin uses the resource-intensive hashcash proof-of-work function based on the SHA-256The Secure Hash Algorithm with an output size of 256 bits designed by the National Security Agency (NSA) first published by the National Institute of Standards and Technology (NIST) in 2001. for a high level of security.
- The proof-of-work method based on computing power also provides a consensus system as a probabilistic solution to the Byzantine Generals’ ProblemA scenario where some parties in a distributed network may not be trustworthy, and any node or message that is false or corrupt may result in an attack or collapse of the network. – a classic trust problem faced by any distributed network.
- Bitcoin mining is designed to be difficult and resource-intensive, in order to safeguard the security of the blockchain and discourage a 51% attackan attack on the bitcoin blockchain by a group of miners with more than 50% of the network’s global mining hashrate on the network.
- If bitcoin mining did not consume so much power, the amount of resources and costs to achieve a 51% attack would be proportionately less i.e. a little over half of what it costs. High energy cost is part of what keeps the blockchain secure against unscrupulous parties.
- As at end 2017, the resources required to perform a 51% attack on the bitcoin network was estimated to be around US$30 billion. Such a hack is only hypothetical and has never taken place as it requires a huge amount of money and computing resources, and the attackers would only be able to prevent new transactions, halt payments and reverse transactions or double-spendthe scenario where bitcoin or other cryptocurrencies are spent twice, without the ability to create new coins or alter previous blocks on the blockchain.
- As more miners get on the Bitcoin network, the resources required to perform a 51% attack today becomes significantly higher. At such a prohibitive cost, hackers will need to consider if it is worthwhile to hack the Bitcoin network at all.
- Large group of miners or mining pools are also discouraged from deploying hashrates approaching 50% of the network strength as this brings about fear in the bitcoin community that the network may be compromised or manipulated. This would then in turn devalue bitcoin as a cryptocurrency, including the current bitcoin holdings of these miners. This deters human greed and ensures fairness in distribution to a great extent.
- As such, large mining pools would rarely approach 30% of the network strength (see Fig. 1.6b below), even when they have the capabilities and means to do so, for the reasons stated above. You could say the bitcoin network looks after itself pretty well in preventing deceit and subterfuge.
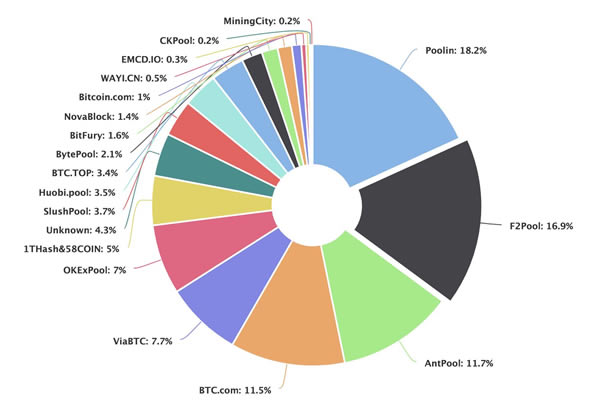
Fig. 1.6b The hashrate distribution chart showing the largest mining pools and their respective hashrates on the Bitcoin network. Mining pools would rarely approach 30% of the network strength to prevent jeopardising the trust in the network. Source: www.blockchain.com/pools
So far we have seen how bitcoin mining creates new bitcoin and validates transactions on the blockchain, and how the blockchain helps to keep the bitcoin network secure.
In the next section 1.7 Why Use Bitcoin, we look at the features and characteristics of bitcoin as a store of value and payment system, and how and why it is better than traditional monetary systems.

 World's No.1
World's No.1